The OpenVPN wizard is a convenient way to setup a remote access VPN for mobileclients. It configures all of the necessary prerequisites for an OpenVPN RemoteAccess Server:
- The recommended method to install the OpenVPN Access Server is to use the official OpenVPN Access Server software repository. You will need to be logged on to your Linux system either on the console or via SSH, and have root privileges.
- In case VPN server runs within an isolated environment group the VPN client will only have access to the environments of this group Install Let’s Encrypt free SSL with auto-renewal for OpenVPN Admin Web Server - this option installs the Let’s Encrypt Free SSL add-on on the VPS server and issues valid SSL certificate for the environment.
- Sep 17, 2020 OpenVPN Remote Access Configuration Example¶ The OpenVPN wizard is a convenient way to setup a remote access VPN for mobile clients. It configures all of the necessary prerequisites for an OpenVPN Remote Access Server: An authentication source (Local, RADIUS server, or LDAP server) A Certificate Authority. A Server Certificate.
- OpenVPN First Time Access - This is a shortcut to that will help you get started. It will open the webpage in your computer's default web browser. It will open the webpage in your computer's default web browser.

An authentication source (Local, RADIUS server, or LDAP server)
A Certificate Authority
A Server Certificate
An OpenVPN server instance.
OpenVPN Access Server by OpenVPN Technologies, Inc. Is a full-featured SSL VPN software solution that integrates the open-source OpenVPN server capabilities with additional features. Those features include a simplified administration web interface and automated certificate management to easily issue user certificates and keys without.
By the end of the wizard a fully functioning sever will be configured and readyfor users. An example setup will be used to aide in explaining the optionsavailable in the wizard.
Before Starting The Wizard¶
Before starting the wizard to configure the Remote Access Server,there are some details that must be planned.
Determine an IP addressing scheme¶
An IP subnet must be chosen for use by the OpenVPN clients themselves. This isthe subnet filled in under Tunnel Network in the server configuration.Connected clients will receive an IP address within this subnet, and the serverend of the connection also receives an IP address used by the client as itsgateway for networks on the server side.
As always when choosing internal subnets for a single location, ideally thechosen subnet will be designed so that it can be CIDR summarized with otherinternal subnets. The example network depicted here uses 10.3.0.0/24 for LAN,and 10.3.201.0/24 for OpenVPN. These two networks can be summarized with10.3.0.0/16, making routing easier to manage. CIDR summarization is discussedfurther in CIDR Summarization.
Example Network¶
Figure OpenVPN Example Remote Access Network shows the networkconfigured in this example.
Choose Authentication Type¶
On the first screen of the OpenVPN Remote Access server wizard, choose a methodfor user authentication. The choices available for Authentication BackendType are Local User Access, LDAP, and RADIUS.
If an existing authentication system is already in place, such as ActiveDirectory, pick LDAP or RADIUS depending on how that system is configured.Local User Access may be selected to manage the users, passwords, andcertificates on the pfSense® firewall. When using Local User Access, per- usercertificates may be used easily, managed completely in the pfSense GUI. This ismuch more secure, but depending on the number of users which will access theservice, may be less convenient than using a central authentication system.
Note
For LDAP or RADIUS, per-user certificates cannot be used withoutgenerating them manually.
The Local User Access choice is the equivalent of choosing Remote Access(SSL/TLS + User Auth) mentioned earlier in this chapter. LDAP and RADIUSare equivalent to Remote Access (User Auth).
After selecting the authentication server type, click Next. If LDAP orRADIUS were chosen the server configuration for those choices will be the nextstep. If Local User Access was chosen, the LDAP and RADIUS wizard steps areskipped. For this example, Local User Access will be chosen, but the otheroptions are discussed for completeness.
Choosing an LDAP Server¶
If an LDAP server is already defined on the pfSense firewall it may be chosenfrom the list. To use a different LDAP server instead choose Add new LDAPserver. If there are no LDAP servers defined, this step is skipped.
Adding an LDAP Server¶
If no LDAP servers exist or Add new LDAP server is chosen a screen will bepresented with the options needed to add a new server. Many of these optionswill depend on the specific LDAP directory configuration and structure. If thereis any uncertainty about the settings, consult the LDAP server administrator,software vendor, or documentation.
Note
The details of LDAP servers are covered inAuthentication Servers. Some detail is omitted heresince the options are discussed in-depth elsewhere. For more information onthe options listed in this section, refer there instead.
Descriptive name for this LDAP server, for reference.
The hostname or IP address of the LDAP server.
The port on which the LDAP server may be contacted. The default port is 389for standard TCP connections, and 636 for SSL.
This can be set to TCP - Standard for unencrypted connections, orSSL - Encrypted for secure connections. A standard connection may besufficient at least for local servers or initial testing. If the server isremote or crosses any untrusted network links, SSL is a more secure choice.If SSL is to be used, the CA Certificate from the LDAP server must beimported into pfSense, and the Hostname or IP address above must matchthe value in the Common Name field of the server certificate.
Selects how deep to search in the LDAP directory, OneLevel or Entire Subtree. Most commonly, Entire Subtree is the correctchoice.

The Distinguished Name upon which the search will bebased. For example DC=example,DC=com
These values specify where in the directory thatusers are found. For example, it may be CN=Users;DC=example.
The Distinguished Name for a user that can be used to bindto the LDAP server and perform authentication. If this is left blank, ananonymous bind will be performed, and the password setting below will beignored.
The password to be used with the LDAP Bind User DN.
Varies depending on the LDAP directory software andstructure. Typically cn for OpenLDAP and Novell eDirectory, andsamAccountName for Microsoft Active Directory.
Varies depending on the LDAP directory software andstructure, but is most typically cn.
Varies depending on the LDAP directory software andstructure. Typically member on OpenLDAP, memberOf on Microsoft ActiveDirectory, and uniqueMember on Novell eDirectory.
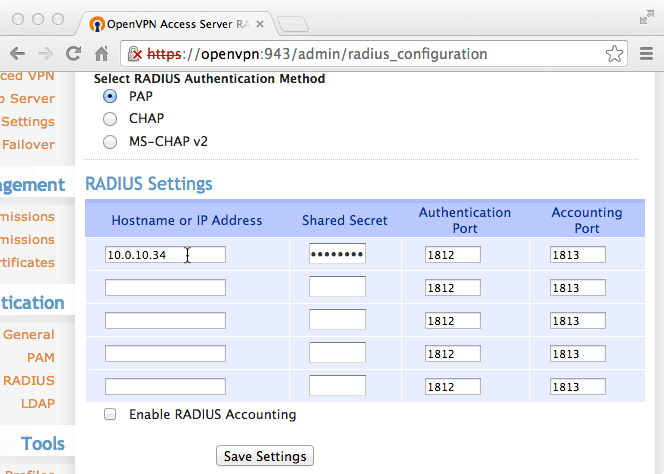
Choosing a RADIUS Server¶
If there is an existing RADIUS server defined on the pfSense firewall, choose itfrom the list. To use a different RADIUS server, instead choose Add new RADIUSserver. If no RADIUS servers are defined on pfSense, this step is skipped.
Adding a RADIUS Server¶
If no RADIUS servers exist, or Add new RADIUS server was selected, a screenis presented with the options needed to add a new server. If there is anyuncertainty about the settings, consult the RADIUS server administrator,software vendor, or documentation.
Note
The details of RADIUS servers are covered inAuthentication Servers. Some detail is omitted heresince the options are discussed in-depth elsewhere. For more information onthe options listed in this section, refer there instead.
Descriptive name for this RADIUS server, for reference.
The hostname or IP address of the RADIUS server.
Port used by the RADIUS server for acceptingAuthentication requests, typically 1812.
The Shared Secret is the password configured on the RADIUSserver for accepting authentication requests from the IP address of thepfSense firewall.
Choosing a Certificate Authority¶
If there is an existing Certificate Authority defined on the pfSense firewall,it may be chosen from the list. To create a new Certificate Authority, chooseAdd new CA. If no Certificate Authorities are defined, this step is skipped.
Creating a Certificate Authority¶
This step presents all of the necessary fields to create a new certificateauthority (CA). Every option on this page is required, and all fields must befilled out correctly to proceed. The CA is used to establish a trust base fromwhich the server certificates can be generated and deemed “trustworthy” byclients. Because this CA is self-generated, it will only be trusted by clientswho are also supplied with a copy of this CA certificate.
See also
For more information on creating and managing CAs, seeCertificate Authority Management.
A name for reference to identify this certificate. This isthe same as Common Name field for other Certificates. For this example CA,ExampleCoCA is used. Although using spaces in this field is allowed, westrongly discourage using spaces in a Common Name field because some clientshave issues handling them properly.
Size of the key which will be generated. The larger the key, themore security it offers but larger keys are generally slower to use. 2048is a good choice.
The time in days that this CA will be valid. On a self-generated CAsuch as this, it is commonly set to 3650, which is approximately 10years.
Two-letter ISO country code (e.g. US, AU, CA). If the two-letterISO country code is unknown, locate it on the ISO Online Browsing Platformsite. Since the ExampleCo company is set in the United States, enter USfor this example.
Full unabbreviated State or Province name (e.g. Texas,Indiana, California). ExampleCo is located in Texas for this example.
City or other Locality name (e.g. Austin, Indianapolis, Toronto).ExampleCo’s headquarters is in Austin.
Organization name, often the Company or Group name. ExampleCogoes here for this example. Do not use any special characters in thisfield, not even punctuation such as a period or comma.
E-mail address for the Certificate contact. Often the e-mail of theperson generating the certificate, such as vpnadmin@example.com.
Click Add new CA to finish the CA creation process
Choosing a Server Certificate¶
If there is an existing Certificate defined on the pfSense firewall, it may bechosen from the list. To create a new Certificate, choose Add newCertificate. If no Certificates are defined, this step is skipped.
Adding a Server Certificate¶
This screen creates a new server certificate which will be used to verify theidentity of the server to the clients. The server certificate will be signed bythe certificate authority chosen or created previously in the wizard. In mostcases, as with this example, the same information from the previous step isused and it will be pre-filled on the form automatically.
This is the Common Name (CN) field for the server certificateand is also used to reference the certificate in pfSense. Using the hostnameof the firewall is a common choice for a server certificate, such asvpn.example.com. Although using spaces in this field is allowed, westrongly discourage using spaces in a Common Name field because clients tendto have issues handling them properly.
Size of the key which will be generated. The larger the key, themore security it offers but larger keys are generally slower to use. 2048is a good choice.
Lifetime in days. This is commonly set to 3650 (Approximately 10years).
Two-letter ISO country code (e.g. US, AU, CA)
Full State of Province name, not abbreviated (e.g. Texas,Indiana, Ontario).
City or other Locality name (e.g. Austin, Indianapolis, Toronto).
Organization name, often the Company or Group name. Do not useany special characters in this field, not even punctuation such as a periodor comma.
Openvpn Access Server Download
E-mail address for the Certificate contact. Often the e-mail of theperson generating the certificate. (e.g. vpnadmin@example.com)
Click Create New Certificate to store the settings and continue to the nextstep of the wizard.
Configuring OpenVPN Server Settings¶
The options on this step of the wizard configure each aspect of how the OpenVPNserver itself will behave as well as options which are passed on to clients. Theoptions presented here are the same as those discussed previously inOpenVPN Configuration Options, refer to that section fordetails. Because the options are covered in detail in that section, only thesettings for this example will be mentioned.
General OpenVPN Server Information¶
These options control how the OpenVPN instance operates.
Since incoming connections will be from the WAN side, select WAN.
The default of UDP is acceptable.
This will be the first OpenVPN server instance so the default of1194 is preferred. If there is an existing OpenVPN on that port, use adifferent port number. The wizard will suggest an unused port number.
As this will be for remote user access, ExampleCoMobileVPNClients is a fitting description.
Cryptographic Settings¶
These options control how traffic in the tunnel is encrypted and authenticated.
TLS is highly desirable so check Enable authentication ofTLS packets.
There is no existing TLS key, so check Automaticallygenerate a shared TLS authentication key.
Since there is no existing TLS key, leave this blank.
Select 2048, as it is good balance of speed andstrength.
This can be left at the default value of AES-128-CBC,but any other option would also work well as long as the clients are set tomatch.
Leave at the default SHA1 (160-bit)
The target device has no accelerator, so leave this set to NoHardware Crypto Acceleration
Tunnel Settings¶
These options control how traffic coming from the remote clients will be routed.
As in the diagram at the start of this example, the subnet10.3.201.0/24 has been chosen for the VPN clients.
For ExampleCo’s setup, The VPN will only carry traffic whichis destined for the subnets at the main office so this box is leftunchecked.

This is the main office subnet, which in this example is10.3.0.0/24.
ExampleCo does not want to limit the number of clientswhich can connect at the same time, so this is left blank.
To improve throughput of traffic on the VPN tunnel at the expenseof some CPU power, this is set to Enabled with Adaptive Compression.
This box is unchecked, as there is no traffic on this VPNwhich requires prioritization/QoS.
Because the clients on this VPN have no need toconnect to other client machines, this box is unchecked.
Because unique certificates exist for every client, thisis unchecked.
Client Settings¶
These options control specific settings given to the clients when a connectionis established.
The clients will connect from all over the country and unknownmobile networks and their IP addresses are likely to change without notice sothis option is checked.
The clients will be assigned addresses from the tunnel networkabove, so this is checked.
The method used to assign IP addresses to clients. The default ofSubnet is the best choice.
Enter the domain for ExampleCo here, example.com.
Openvpn Access Server Admin Web Ui
Any internal DNS server could be used here. ExampleCo has aWindows Active Directory Domain Controller which is configured to act as aDNS server, 10.3.0.5.
The server above, 10.3.0.5, is also used to synchronize clientPC clocks.
Clients will need access to Windows shares behind the VPN, socheck Enable NetBIOS over TCP/IP.
Because DNS is used primarily, select h-node.
This will be left blank, since the NetBIOS scope is notlimited.
WINS has been deprecated, so this is left blank.
At this time no additional tweaks are needed, so this is left blank.
Firewall Rule Configuration¶
As with other parts of the firewall, by default all traffic is blocked fromconnecting to VPNs or passing over VPN tunnels. This step of the wizard addsfirewall rules automatically to allow traffic to connect to the VPN and also soconnected clients can pass traffic over the VPN.
Traffic from clients to server¶
Check this box to add a firewall rule on the chosen interface for the tunnel(e.g. WAN) which lets clients connect. It allows all clients from any sourceaddress to connect by default. To allow connections from a limited set of IPaddresses or subnets, either make a custom rule or check this box and alter therule it creates. Since in this example clients are connecting from all over thecountry, the rule created by this checkbox is ideal, so the box is checked.
Traffic from clients through VPN tunnel¶
This setting allows all traffic to cross the OpenVPN tunnel, which is desirablefor this example, so this box is checked.
Finishing the Wizard¶
Click Finish and the wizard is now complete; The tunnel is fully configuredand ready for client connections. From here the next steps are to add users andconfigure client devices. If adjustments to the automatically generated firewallrules are required, make them now.
Verifying the Setup¶
Look at firewall rules (WAN and OpenVPN tabs)
WAN tab rule should pass from any to the OpenVPN port on theWAN address
OpenVPN tab rule should allow anything from any/to any
Adjustments¶
Some settings are not presented in the wizard but might be a better fitfor some situations than the defaults chosen by the wizard.
Server Mode¶
The OpenVPN Server Mode allows selecting a choice between requiringCertificates, User Authentication, or both. The wizard defaults toRemote Access (SSL/TLS + User Auth). The possible values for thischoice and their advantages are:
Remote Access (SSL/TLS + User Auth)
Requires both certificates AND username/password
Each user has a unique client configuration that includes theirpersonal certificate and key.
Most secure as there are multiple factors of authentication (TLSKey and Certificate that the user has, and the username/passwordthey know)
Remote Access (SSL/TLS)
Certificates only, no auth
Each user has a unique client configuration that includes theirpersonal certificate and key.
Useful if clients should not be prompted to enter a username andpassword
Less secure as it relies only on something the user has (TLS keyand certificate)
Remote Access (User Auth)
Authentication only, no certificates
Useful if the clients should not have individual certificates
Commonly used for external authentication (RADIUS, LDAP)
All clients can use the same exported client configuration and/orsoftware package
Less secure as it relies on a shared TLS key plus only somethingthe user knows (Username/password)
Certificate Revocation¶
Compromised certificates can be revoked by creating a CertificateRevocation List (CRL) in System > Cert Manager on the CertificateRevocation tab, adding the certificate to it, and then selecting thatCRL on the OpenVPN server settings.
Adding a User with a Certificate¶
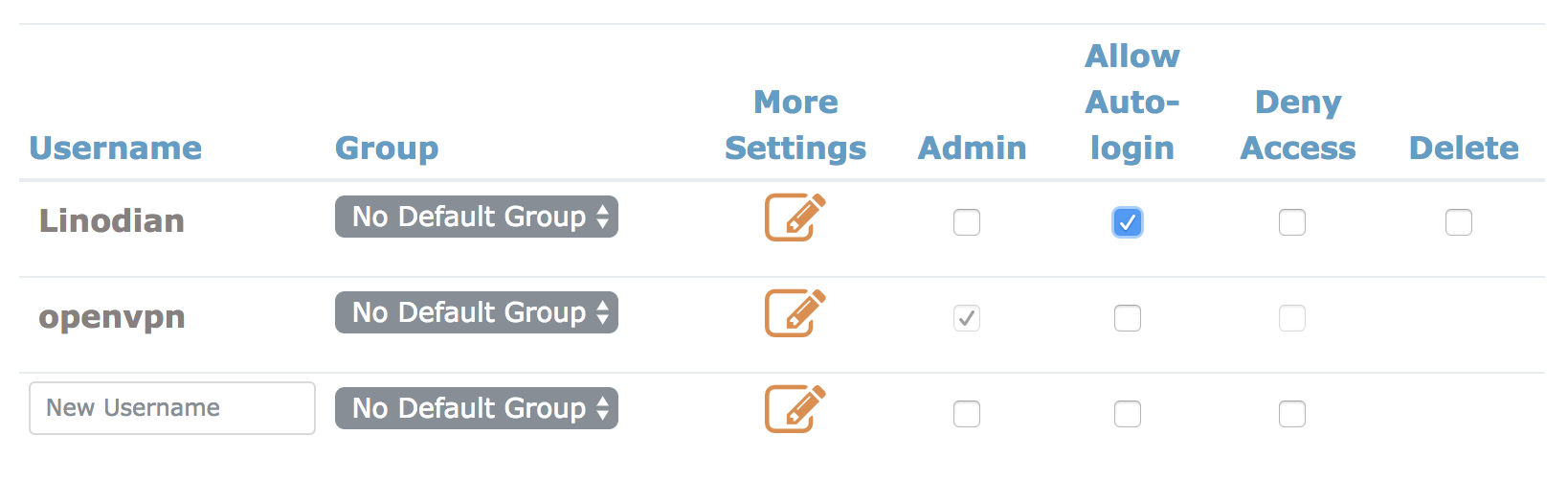
If the mode has been left at the wizard’s default or on a mode thatincludes local user authentication, a user must be created in the usermanager.
Navigate to System > User Manager
Click To add a user
Fill in Username
Fill in Password / Confirm password
Check Click to create a user certificate.
Fill in the Descriptive Name as the username
Choose the appropriate Certificate Authority
Click Save
OpenVPN Client Export Package¶
The OpenVPN Client Export Package allows exporting configurationsformatted for a wide variety of platforms. It also allows exporting apre-packaged Windows installer executable which includes theconfiguration bundled inside for a painless client installation.
See OpenVPN Client Export Package for more.
Related
Join the DigitalOcean CommunityJoin 1M+ other developers and:
- Get help and share knowledge in Q&A
- Subscribe to topics of interest
- Get courses & tools that help you grow as a developer or small business owner
Question
I have a fresh install of Debian Lamp server, everything works perfectly (Web server, mysql etc). Note: Before I proceed with OpenVPN installation I took a snapshot of my server.
Then I wget the package of OpenVPN and then dpkg -i as their instructions advised.
The first time I installed it I was able to login to the admin panel and do stuff. But i tried to change the hostname in the OpenVPN settings (instead of my IP I set my domain (domain.name.com)) since then I have no access on the Openvpn. I tried to telnet myip 943 and it response with connection refused. I even restored back to the snapshot and proceed with the same steps of installation of OpenVPN and no luck. I dont understand, why this is happening. Even with restoring the server from the snapshot prior the installation did not solve the problem. Any suggestions?
Related
Join the DigitalOcean CommunityJoin 1M+ other developers and:
- Get help and share knowledge in Q&A
- Subscribe to topics of interest
- Get courses & tools that help you grow as a developer or small business owner
These answers are provided by our Community. If you find them useful, show some love by clicking the heart. If you run into issues leave a comment, or add your own answer to help others.
×
Comments are closed.